Ransomware is on the rise, and its targets range from individuals to government and law enforcement agencies. Hacking and generally malicious cyber activity has always been lucrative for cyber terrorists who often use stolen information to commit identity fraud, or sell sensitive information to third parties. Ransomware is the latest form of malware to capitalize on the potential gains of cybercrime by requesting that victims pay to have their own computers or files unlocked for use.
That’s right. They ask you to pay your own ransom.
To better understand this growing threat, let’s look at what ransomware is and what it means to those it targets.
Why Content Filtering Keeps Employees Productive
Keeping employees productive means no wasted resources. It means a more efficient work place where deadlines are met. Better productivity doesn’t only benefit the CEOs and their bottom line, either; it’s also good for the employees. Feeling a sense of accomplishment and feeling productive can help foster better work ethic and a positive self-image.
Having days where we feel lazy or have gotten distracted at work can lead to feeling worse about ourselves and can even cost us our jobs. We feel good when we finish a task on time or ahead of schedule, so it makes sense to form habits at work that contribute to that general sense of accomplishment. With so many offices relying on computers, the internet can prove to be one of the largest obstacles in the way of our productivity. This is where content filtering comes in.
Mobile Malware on the Rise
Some people might be surprised to find that even their mobile devices aren’t safe from malware. Malicious software is no longer confined to desktop computers and the rate of infection for mobile devices is on the rise. As mobile browsing becomes more common and users are able to do more from their smartphones and tablets, hackers have found a new tool with which to wreak havoc: mobile malware.
Kaspersky Lab, a cybersecurity company, reported that their mobile products alone detected a total of 103,072 new malicious programs in the Q1 2015.
Three times the amount they found in Q4 2014.
With cyberterrorists finding newer ways to abuse and exploit the browsing behavior of mobile users it’s important for executives and consumers alike to understand what mobile malware might look like and how they can better protect themselves from it.
Avoid Headaches When Upgrading to Windows 10
The buzz surrounding Microsoft’s Windows 10 shouldn’t be anything new to those considering the newest upgrade. You’ve either been pressured by the little box on the bottom right of your screen to make the switch, or you can’t escape the office debates, but no matter how you look at it, upgrading to Windows 10 is a big deal.
Of course you could say the same about any major software or Operating System (OS) upgrade. But when it comes to your OS, you absolutely have to weigh the pros and cons before making the decision to stay or upgrade.
Upgrading too soon can cause frustration and downtime. Neither of which will make the lives of your coworkers or customers any easier. Computers are an integral part of your business, understanding the risks inherent in any OS upgrade is critical in mitigating problems associated with the installation.
We recommend waiting at least six months between the dates the software is released and installing it. Because that six months is almost up (January 29th being the six-month mark of its release) for Windows 10, we came up with a list of the four main talking points—and their pros and cons—to help you avoid the pain of a botched upgrade to Windows 10.
Missing These Opens Up Your Computer to Cyber-Attacks
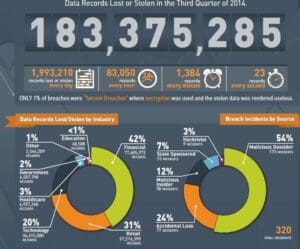
Cyber-attacks have been a plague throughout the world this past year, whose victims include government agencies, businesses, international banks, and citizens. No one seems safe from data breaches, and because so many of these cyber terrorists evade capture, the problem seems unending. Anonymous hackers breach servers to dump terabytes of sensitive information, and their victims—often collateral damage—have their social security numbers, emails, names, and more displayed, sold, or exposed for the world to see.
In the business world, a breach in your computer security can lead to lost revenue, costly downtime, or even a loss of customers when sensitive company and client information is stolen. Typical dangers range from simple data theft and damaging malware attacks to cyber mischief meant to wreak havoc on your servers, weeks or even months after the initial breach. The most startling aspect of these dangers is how easily they infiltrate computers and servers, sometimes lingering in the background as they mine for data and record user information—all without your knowledge.
Hiring professional security is common practice for companies looking to protect warehouses full of goods, so why shouldn’t businesses extend the same protection to their valuable data? Securing your networks against cyber threats isn’t just about safeguarding information—it’s about assuring others that your company won’t experience sudden downtime or a halt in productivity due to a breach.
Below are four must-have factors if you want to dodge the next cyber-attack.
Top 5 Worst High-Tech Habits to Break in 2016
Admit it – you have some bad habits when it comes to maintaining the security and health of the high-tech tools your business depends on everyday. Since it’s a fresh new year, we thought this would be a great time to point out some of the most popular bad habits most businesses should be working on in 2016.
10 Smartphone Security Tips
For better or worse we are all practically “married” to our phones these days. Our phones go everywhere we go and have access to our most private conversations as well as our most precious memories. But as useful as our phones are, they can also make us vulnerable to attacks by thieves and cyber-criminals determined to access our private information for personal gain.
So how can you use these smartphone security tips and avoid being manipulated or attacked by cyber-criminals? Here are some smart tips to keep your smartphone safe.
The Most Shocking Threat to Your Lancaster, Harrisburg, or York Small Business Security
Hopefully by now you realize you need to keep a close watch over the security of your PC and other devices (or you’re smart enough to hire us to do it for you). Either way, cyber-crime is BIG business, and small business owners are seen as the low hanging fruit by attackers who are looking for easy-to-steal financial data, passwords and more.
But there’s a much bigger threat to small business data security that can not only leak your information out to the masses, but can also corrupt or erase data, screw up operations and bring everything to a screeching halt.
What is it? Surprisingly, it’s your employees.
Here are just some of the ways your employees could be compromising your business’s security and what you can do about it.
How Long Would It Take To Crack Your Password?
Think about your strongest password. Does it contain more than one non-numeric symbol? How many characters long is it? Most important: can you REMEMBER your strongest password (without writing it down on a sticky note stuck to the corner of your PC screen)?
Protecting your online information and computer can easily boil down to having a strong enough password. What, then, makes a password strong? Password strength is a combination of letters, numbers, and symbols you use, or about meeting the minimum or maximum character length. Really, a strong password is a long password.
The Three Biggest IT Mistakes Local Businesses Make
Want to avoid the most common and expensive computer problems most local business owners experience? Then read on! We’ve compiled a list of 3 things you should be doing to save yourself a lot of time and money, by avoiding a big, ugly computer disaster.